Sometimes I like to go back to the basics, for network troubleshooting a good packet analyzer is what I need. I use Wireshark and Tshark if I can, but sometimes I get everything I need out of TCPDUMP. Sometimes I find myself staring at a Windows machine and not at a Linux command line. No problem, Windows has a couple of useful shells to work with, and it can run something very very close to TCPDUMP.
So, if you are also looking for a simple alternative to Message Analyzer, Wireshark, or Tshark than WinDump – (a port of LibPcap ) may be just what you’re looking for. If you are familiar with TCPDUMP on Linux or UNIX than you will find WinDump works very much the same.
verify your download:
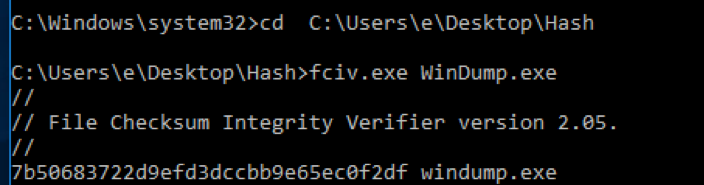
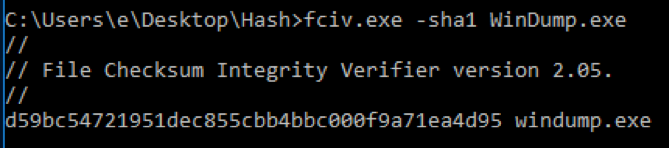
SHA1: d59bc54721951dec855cbb4bbc000f9a71ea4d95
MD5: 7b50683722d9efd3dccbb9e65ec0f2df
You can use Sigcheck to verify the file:
https://download.sysinternals.com/files/Sigcheck.zip
Also available is the entire suite of System Internal Tools which also contains SigCheck
https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
Another available but currently unsupported command-line utility that computes MD5 or SHA1 cryptographic hashes for files that work with Windows 10:
Microsoft File Checksum Integrity Verifier tool
(Windows-KB841290-x86-ENU.exe)
https://www.microsoft.com/en-us/download/details.aspx?id=11533
I find it easier to place both WinDump and fciv in the same folder.
You may choose to move WinDump after you scan your download with antivirus and/or Malware detection tool and verify the file integrity
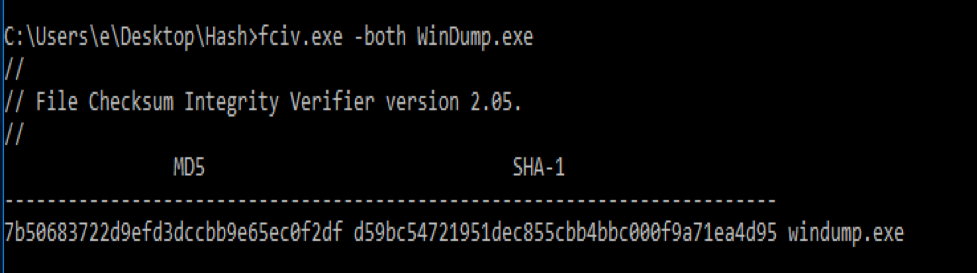
Using “-both” to see both the SHA1 and MD5 output together
You can find the manual for WinDump (actually its also the TcpDump manual) at:
https://www.winpcap.org/windump/docs/manual.htm
windump.exe version 3.9.5, based on tcpdump version 3.9.5
WinPcap version 4.1.3 (packet.dll version 4.1.0.2980), based on libpcap version 1.0 branch 1_0_rel0b (20091008)
Usage: windump.exe [-aAdDeflLnNOpqRStuUvxX] [ -B size ] [-c count] [ -C file_size ]
[ -E algo:secret ] [ -F file ] [ -i interface ] [ -M secret ]
[ -r file ] [ -s snaplen ] [ -T type ] [ -w file ]
[ -W filecount ] [ -y datalinktype ] [ -Z user ]
[ expression ]
If you’re interested in what’s new with Tcpdump and LibPcap check out the latest releases:
http://www.tcpdump.org/#latest-releases
If all you want to do is collect packet data (with low overhead) so that you can examine the capture later in Tshark or Wireshark, and you have Wireshark tools installed than Dumpcap is another useful option. I believe on Linux, TcpDump may drop fewer packets than Dumpcap (and Tcpdump can parse data in near real-time for viewing), so I would lean more toward using WinPcap on Windows machines if available. You may find that Tshark and Dumpcap work better for your system, but I tend to use either Tcpdump/WinDump or Wireshark. I will use Tshark on occasion, but rarely would I limit my use to Dumpcap only.
