The philosophy of doing more with less sounds good, but it is not always practical. It takes effort and lots…
Wireshark
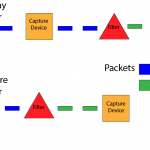
Wireshark Filters: Display vs Capture
A common thought by beginners when it comes to Wireshark filters is that display and capture filters do the same…

Wireshark Basic Overview
What is Wireshark? Wireshark is open-source software for Windows and UNIX/Linux, open-source meaning that anyone can download it for free…